| Did a friend forward this to you through an unencrypted radio transmission? Sign up here. One of the challenges that Russia has faced in its effort to subdue — to subsume — Ukraine is that it has proved to be unprepared for the technological moment. For all of the fulminating before the war about Russia's ability to hobble Ukraine's Internet infrastructure or to inject disinformation into its opponent's population, it's become apparent that Russia, not Ukraine, is at a disadvantage on modernity. We see this in the information fight, certainly; Ukraine, fighting on friendly ground and with an ongoing connection to the rest of the world, has effectively framed the conflict in sympathetic terms. But it's also true in how Russia has trailed in using technology to conduct its war and in how technology is helping to hold Russia accountable. Consider a recent post from the author of the newsletter Line of Actual Control. (I'll call him LOAC moving forward, as his employer allows him to write but not using his actual name.) It's one of the most remarkable examples of open-sourced investigation that I've ever seen. It began with tweets like this one. That's hard to parse out of context, but it, by itself, is a fascinating document. That Twitter user, @xateond, listens to unencrypted radio chatter over the Internet and posts what he hears. In other words, while modern militaries like the United States' have systems to protect communications between commanders and soldiers, Russia often doesn't, allowing anyone — even people on the other side of the world — to listen in. It's roughly the difference between sending someone a text message on your iPhone and sending someone a postcard. What @xateond is publishing appear to be coordinates: target 133, x — referring to a horizontal coordinate — 84 620 and y (a vertical coordinate) 27 700. LOAC was curious if the numbers actually meant anything. "I started thinking about how to visualize these coordinates, or at the very least, understand if they are coordinates in the first place," he told me in a phone call. "And that's where the grid came in." He took the numbers recorded by @xateond and put them in a simple Excel table. What emerged was an obvious pattern: It wasn't just random coordinates but, instead, clusters of locations. Now, he had to figure out what the coordinates themselves correlated to. 84 what? 27 what? These weren't latitudes and longitudes. As it turns out, the answer was readily available: Russian military maps use similar coordinate positions. You can see them, for example, in these captured Russian maps that were shared on Twitter. The coordinates in the tweet above indicate a position near Mariupol in southeastern Ukraine — one of the places where fighting and shelling has been heaviest. Next, LOAC took his Russian map and overlaid it on known satellite imagery of the area and put his Excel grid of coordinates on top. All three lined up. 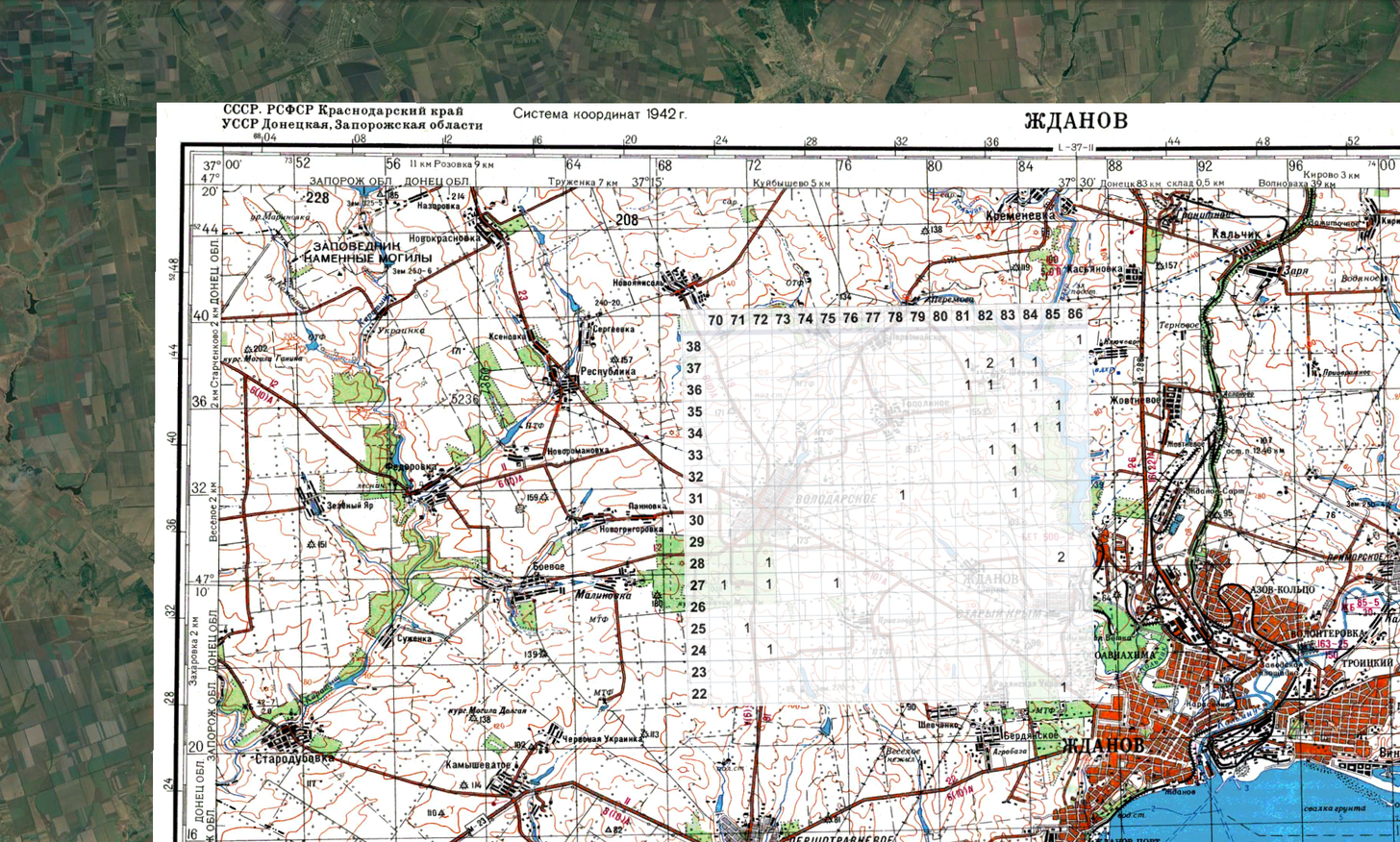 A stack of three images: satellite imagery at bottom, a Russian map of the region above that and LOAC's Excel spreadsheet on top. (Line of Actual Control) | Here, for example, LOAC shows how one place that was located twice in the overheard chatter (hence the 2) lines up with satellite photographs: the southern end of a reservoir at top (in circle) and a small village in the large rectangle at bottom. The 2 aligns with a field just west of a small lake or pond.  Detail from the stacked maps and satellite imagery. (Line of Actual Control) | Most of LOAC's newsletters focus on satellite imagery, so he was able to pull images from before and after the period at which the coordinates were sent out over radio. And what he found was striking: Just to the west of that small lake, right where the 2 had been, a patch of dark earth now appeared — as though burned.  Comparison of the region above before and after an apparent artillery strike. (Line of Actual Control) | The implication is clear. The coordinates @xateond was sharing were probably artillery strike directions. Over and over, LOAC's investigation of the commands led to the discovery of places where damage had been incurred. The other parts of the message were probably meaningful as well, he told me, reinforcing the idea that these were artillery orders. The "target" identifier was probably a unit identifier and the "angle" further instructions on how to target the specific location. This is one of the most striking examples of data visualization that I've ever seen: military orders intended solely to instruct artillery units on attacks that are reverse engineered into geolocated positions of the strikes from halfway around the world. It's certainly an indication of Russia's failure, yes — but also of the remarkable ingenuity that can accompany a clever use of technological tools. |