| Welcome to The Cybersecurity 202! Check out this great photo of Ukrainian flags flying up and down Pennsylvania Avenue in advance of last night's State of the Union address. Below: Ukraine wants to cut Russia off from the Internet and the D.C. Council is cracking down on government workers using encrypted messaging apps. | Despite Biden's cyber-free SOTU, it was a big day for cybersecurity on the Hill |  Sen. Gary Peters (D-Mich.) speaking Tuesday at the U.S. Capitol. (Photo by Bill O'Leary/The Washington Post) | | | The big cyber energy wasn't at the State of the Union address last night but rather in the Senate. A few hours before President Biden's speech, the chamber passed the most significant cyber legislation in history — including a mandate for companies in critical sectors to alert the government when they're hacked or when they pay ransoms to hackers. That measure narrowly failed to become law last year amid senatorial squabbling. But it zipped over the finish line this time — spurred partly by rising anxiety about Russian cyberattacks following the invasion of Ukraine and punishing sanctions imposed by the United States and its allies. "As our nation continues to support Ukraine, we must ready ourselves for retaliatory cyberattacks from the Russian government," Senate Homeland Security Chairman Gary Peters (D-Mich.), a lead sponsor of the bill, warned. | | @SenGaryPeters | "As our nation continues to support Ukraine, we must ready ourselves for retaliatory cyberattacks from the Russian government." | | | | | | | | He called the bill "a significant step forward to ensuring the United States can fight back against cybercriminals and foreign adversaries." | - A measure that updates the 20-year-old rules for how government agencies manage their information security
- Another measure that updates how the government assesses and manages the cybersecurity of cloud computing systems federal agencies use
| | The House has not yet passed its version of the cyber reporting measure, but the chances seem good. The chamber easily included a version of the measure as an amendment to a must-pass defense policy bill last year, when the Senate fumbled it at the finish line. The measure marks a sea change for how government deals with cyberthreats. It's the first time Congress has imposed a cyber mandate across a broad range of critical infrastructure firms — a category that includes companies in energy, transportation, financial services, health care and a variety of other fields. It comes after years of trying to manage cybersecurity almost entirely with companies' voluntary cooperation. That model has led to significant improvements but not kept pace with the incredible growth of cyberthreats, most cyber and policy pros say. How big a change?: The last cyber bill with this broad of an impact on the private sector passed back in 2015 and it merely gave companies legal cover to voluntarily share cyberthreat information with the government. The bill still passed only narrowly, and the idea of stronger measures were basically unthinkable for years after. There are two big goals for the bill. First, the Cybersecurity and Infrastructure Security Agency (CISA) wants to rapidly share big insights from the reports with other companies that might face similar cyberattacks. That can be especially critical during fast-moving events, such as a wave of Russian cyberattacks. | - "At a time when we are facing significant threats of Russian cyberattacks against our institutions and our allies, it's more important than ever that the government have an idea of what those threats are," said Sen. Mark Warner (D-Va.), a supporter of the bill.
| | Second, the bill will give CISA broad insights into how many and what sort of cyberattacks are hitting U.S. companies each day. Those are questions that are frustratingly difficult to answer right now because of major gaps in data breach reporting laws. | - The measure passed despite opposition from some critical infrastructure sectors. They complained that the definition of a "significant cyber incident" in the bill is too vague and that the 24-hour deadline for reports is often too quick to share useful information.
- Senate Majority Leader Chuck Schumer (D-N.Y.) claimed those companies have "come to see the light," on the Senate floor, but there's little evidence their concerns have been completely assuaged.
| | Here's more from Schumer, via Politico's Eric Geller on Twitter: | | |  | Chat room | | | Despite skyrocketing cyber tensions between Russia and the West, Biden made no mention of cybersecurity during his speech last night. Would you like a roundup of cyber reporters complaining about it? Of course you would. | | The Wall Street Journal's Dustin Volz: | 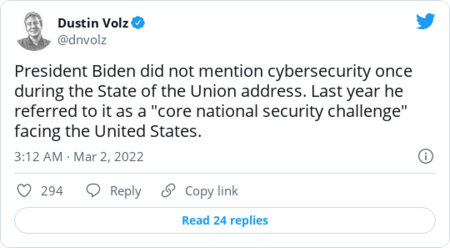 | | | | | Politico's Sam Sabin: | 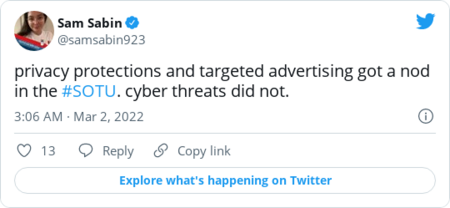 | | | | | The Record's Martin Matishak: | 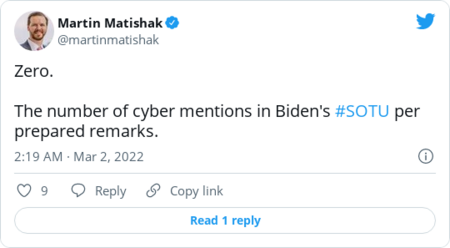 | | | | | CyberScoop's Joe Warminsky: | 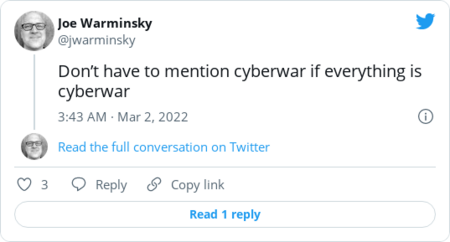 | | | | | |  | The keys | | Ukraine's volunteer cyber army is targeting Russian critical infrastructure |  Smoke rises from the territory of the Ukrainian Defence Ministry. REUTERS/Valentyn Ogirenko | | | The volunteer group of cyber pros, which formed in the wake of Russia's invasion, plans to launch disruptive hacks aimed at railroads, the electric grid and other services that could help Russia move troops and weapons into Ukraine, Reuters's Joel Schechtman, Christopher Bing and James Pearson report. That's a significant escalation from the website takedowns and defacements that the group has primarily focused on so far. But it's far from clear the band of cyber patriots will be capable of causing much damage in Russia, which has relatively advanced digital protections. Targets include "everything that might stop war," Yegor Aushev, a Ukrainian businessman and cybersecurity expert who's helping organize the effort, told Reuters. Experts fear the proliferation of outside groups launching digital attacks in the Ukraine conflict could raise the chances of dangerous errors that might harm civilians or escalate cyber tensions between Russia and the West. | Ukraine wants to cut Russia off from the Internet. Experts say that's a bad idea. |  It comes amid growing pressure around the world aimed at isolating Russian President Vladimir Putin and his government. (Janos Kummer/Getty Images) | | | Ukrainian officials asked Internet governance organization ICANN to shut down use of the ".ru" country code, revoke certificates for those domains and shut down some Russian servers to prevent Russian propaganda from spreading. Those moves would effectively prevent people outside Russia from accessing Russian websites and make it more difficult for people within Russia to access sites outside of the country. But such actions would make ordinary Russians more vulnerable to hackers, experts warn. In particular, it would be easier to surreptitiously spy on their web traffic and harvest any personal information they enter, CyberScoop's Tonya Riley reports. The move would also politicize the fragile balancing act of ICANN, a global group of volunteers who administer the Internet and work mostly by consensus. "It's the complete opposite of what we need," security researcher Runa Sandvik told Tonya. "We should make sure that the Russian people are seeing what is happening and what their government is doing." Ukraine also said it would ask a regional Internet registry to restrict Russian members from using IP addresses. The registry declined and said it will remain neutral, its executive board said: | D.C. Council passes bill to regulate government employee use of messaging apps |  It comes after a report that D.C. Mayor Muriel E. Bowser's (D) administration "widely" used WhatsApp. (Alex Brandon/AP) | | | The legislation is designed to make sure officials' communications on WhatsApp and other messaging apps are subject to public disclosure laws, Michael Brice-Saddler reports. The bill was spurred by a February report by Axios D.C. that found D.C. Mayor Muriel E. Bowser's (D) administration "widely" uses WhatsApp for government communications. "After learning of the use of encrypted messaging apps by members of the executive branch, it is an urgent matter that we boost transparency in District government," said D.C. Council chairman Phil Mendelson (D) when he introduced the legislation. "I get it that many in government would like to conduct their business in private. But that is contrary to long-standing policy. We value open government. We don't value auto-delete." Bowser said she supported efforts to ensure that records are retained ahead of the Council's unanimous vote on the measure. But she criticized the Council for not applying the bill to itself, calling that discrepancy the "height of hypocrisy." Mendelson referenced rules that already require council members to preserve their messages on nongovernment devices. A Bowser spokesperson did not respond to a request for comment about the bill. | | |  | Securing the ballot | | Replacing outdated voting machines around the country would cost hundreds of millions of dollars |  The price tag would exceed $500 million total nationwide to replace voting equipment from 2016 or older, they said. (Evelyn Hockstein for The Washington Post) | | | It would cost more than $350 million to replace voting equipment that is now more than a decade old and likelier to suffer from cyber weaknesses, according to a report from New York University's Brennan Center and the group Verified Voting. | | |  | Global cyberspace | | | |  | Industry report | | | |  | Government scan | | | |  | Daybook | | - Top intelligence and law enforcement officials testify before the House Intelligence Committee on worldwide threats on Tuesday at 10 a.m.
| | |  | Secure log off | | | Thanks for reading. See you tomorrow. | | |